Integrating video surveillance with access control gives security teams complete visibility into who enters their facilities and what actually happens at every door. This guide explains how video access control integration works, the benefits it delivers for multi-site organizations, common integration options, and how to plan a successful deployment.
Table of contents
- What Is AI Video Access Control Integration?
- Benefits of Integrating AI Video Security With Access Control
- Common Video and Access Control Integrations
- How to Choose the Right Platform for AI Video Access Control Integration
- How Lumana Unifies AI Video Security and Access Control
What is AI Video Access Control Integration?
AI video access control integration is the combination of video surveillance systems with credential-based access control into a single, unified security platform. Instead of operating as separate systems, integrated solutions connect door readers, cameras, alarms, and analytics, enabling security teams to visually verify access events and respond to threats in real time.
Standalone access control systems grant or deny entry based solely on credentials like keycards, PINs, or biometric data. While effective at controlling who enters a space, they cannot tell you whether the person using the credential is actually authorized or if multiple people followed through on a single badge swipe.
Integrated systems solve this problem by pairing access events with live and recorded video. Every time someone badges into a door, the system automatically links that event to the corresponding camera footage. This gives security teams complete visibility into what actually happened at every entry point.
Modern integrated platforms go beyond simple pairing of video and access logs. They incorporate AI-powered analytics to detect suspicious behaviors such as tailgating, loitering, or forced entry attempts. When combined with access control data, these analytics enable security teams to identify threats before they escalate rather than reviewing footage after an incident has already occurred.
Benefits of Integrating AI Video Security with Access Control
Organizations that unify their video surveillance and access control systems gain significant advantages in security effectiveness, operational efficiency, and cost management. The integration creates a force multiplier effect where each system enhances the capabilities of the other.
Enhanced security posture and threat detection
Combining video with access control creates a layered defense that addresses vulnerabilities inherent in standalone systems. When someone presents credentials at a door, the integrated system can instantly display live video of that person. Security staff can verify that the credential holder matches the expected identity.
This visual verification catches scenarios that access control alone would miss, such as stolen badges or credentials shared between employees. AI-powered analytics take this protection further by automatically detecting suspicious patterns without requiring constant human monitoring.
- Real-time verification: Security teams can instantly review video when access attempts are flagged as unusual.
- Automated responses: Systems can trigger lockdowns, send alerts, or notify authorities based on detected threats.
- Forensic capability: Complete audit trails link credentials, video, and timestamps for thorough investigations.
Faster incident response and investigation
When security incidents occur, integrated systems dramatically reduce the time required to understand what happened and respond appropriately, with automated alerts reducing response times by 60-80%. Instead of manually searching through hours of video footage while cross-referencing access logs in a separate system, security teams can click on any access event and immediately view the corresponding video.
This centralized approach transforms investigations. A security director can reconstruct exactly what happened at any entry point within seconds. All the evidence needed for compliance reporting or legal purposes is automatically preserved and linked together.
- Centralized data: All security events are logged in one system with automatic cross-referencing between video and access records.
- Rapid investigation: Security teams can reconstruct timelines and identify individuals within seconds rather than hours.
- Evidence preservation: Video and access data are automatically linked to incidents for compliance and legal purposes.
Centralized monitoring across multiple sites
For enterprises and public-sector organizations operating multiple facilities, integrated systems provide unified visibility that would be impossible with standalone solutions. Cloud-based platforms enable security teams to monitor access events and video feeds from every location through a single interface.
Schools, government agencies, manufacturers, retailers, and hospitality brands particularly benefit from this capability. A retail chain can monitor all store entrances from a central security operations center. A school district can oversee every campus from the administrative office.
- Single dashboard: Monitor access events and video feeds across all locations simultaneously.
- Remote management: Adjust permissions, review incidents, and respond to alerts from anywhere with internet access.
- Scalability: Add new locations without redesigning the entire security infrastructure.
This centralized approach also simplifies staffing. Rather than requiring security personnel at every location, organizations can monitor multiple sites with a smaller team working from a central location.
Reduced operational costs over time
While integrated systems may require higher initial investment than standalone solutions, they typically deliver significant cost savings over their operational lifetime. Consolidating multiple systems into a single platform reduces hardware requirements, simplifies maintenance, and improves staffing efficiency.
Organizations also benefit from reduced training costs, as staff need to learn only one system rather than multiple interfaces. The operational expense model of cloud-based platforms further improves budgeting predictability compared to the capital expenditure required for traditional on-premises systems.
- Unified maintenance: One integrated system requires fewer updates and service calls than multiple standalone systems
- Staffing efficiency: Remote monitoring reduces the need for full-time on-site security personnel at every location
- Avoided redundancy: No need to purchase and maintain separate video, access control, and alarm systems
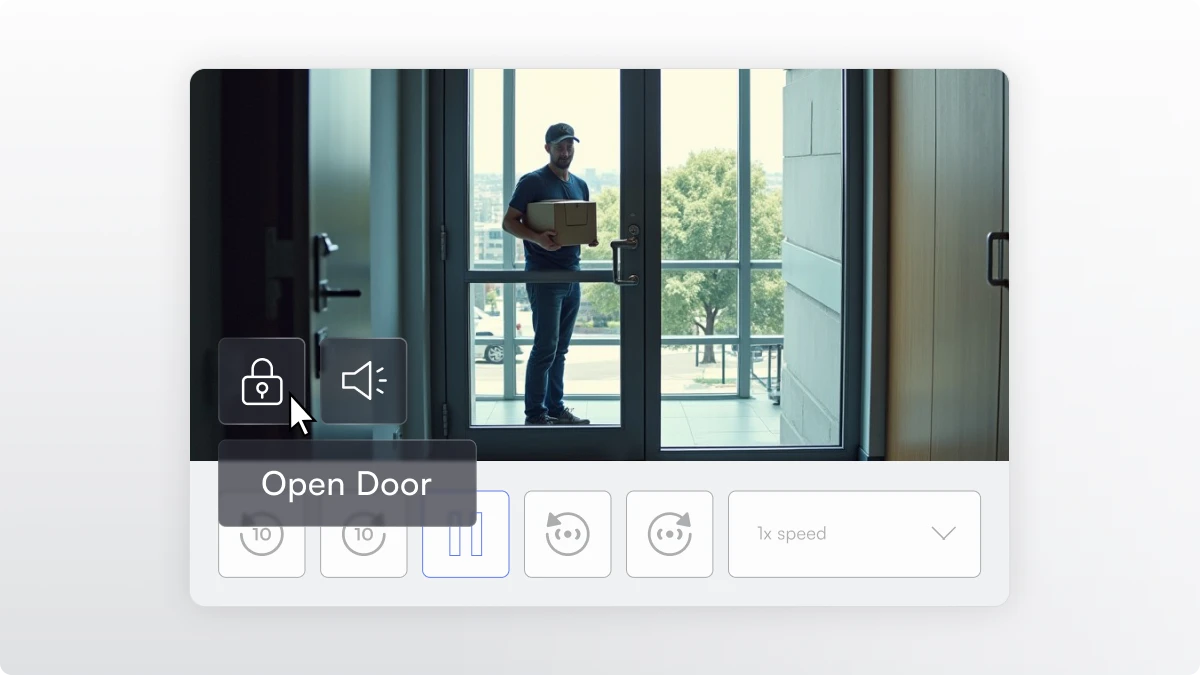
Common Video and Access Control Integrations
Integrated security platforms support connections with numerous complementary systems. Each integration adds specific capabilities that enhance overall protection. Understanding these options helps organizations design solutions tailored to their unique security requirements.
AI-powered video analytics
Artificial intelligence transforms video surveillance from passive recording into active threat detection. AI analytics automatically analyze video feeds to identify suspicious behaviors, unusual patterns, and potential security threats without requiring constant human monitoring.
Modern AI capabilities go far beyond simple motion detection. Systems can recognize specific behaviors, such as someone loitering near a restricted entrance or multiple people attempting to enter with a single badge swipe. When these behaviors are detected, the system immediately alerts security staff.
- Behavior detection: AI identifies unusual activity, such as crowds gathering around sensitive areas, tailgating through secured doors, or forced entry attempts.
- Identity verification: Systems can correlate access credentials with visual identity to verify that the person using a badge matches the authorized user.
- Reduced false alarms: Smart filtering ensures security teams focus on genuine threats rather than routine events.
Intrusion detection and alarm systems
Integrating alarms with access control creates automated response capabilities that activate the moment a threat is detected. Motion sensors, glass break detectors, door contacts, and other intrusion detection devices can trigger immediate access control actions without waiting for human intervention.
For environments like schools and healthcare facilities, this integration supports rapid lockdown procedures that can secure an entire campus within seconds of a threat being detected. The system coordinates video, alarm data, and access logs simultaneously to provide complete situational awareness.
Visitor management solutions
Visitor management systems integrate with access control to streamline the process of welcoming guests while maintaining security. Rather than relying on paper sign-in sheets and manual badge issuance, integrated systems automate the entire visitor experience.
Visitors can be registered, photographed, and issued temporary credentials automatically through self-service kiosks. Their credentials limit access to specific areas and times, preventing unauthorized exploration of facilities. Remote staff can see and communicate with visitors via video intercom before granting access.
This integration is particularly valuable for corporate offices, schools, and healthcare facilities where visitor traffic is high but security requirements remain strict.
Building management systems
Access control integration extends beyond security to connect with building automation systems that manage HVAC, lighting, and energy consumption. This connection enables facilities to operate more efficiently by responding to actual occupancy rather than fixed schedules.
Heating and cooling can activate only when spaces are occupied, reducing energy waste. Lighting adjusts based on real-time occupancy data from access control events. Facilities teams gain insights into how spaces are actually used, informing better planning decisions.
For organizations focused on sustainability and operational efficiency, this integration delivers measurable cost savings while improving occupant comfort.
How to Choose the Right Platform for AI Video Access Control Integration
Not all integrated security platforms are designed for flexibility, scale, or long-term value. Many solutions rely on proprietary hardware, limited analytics, or rigid architectures that restrict growth and innovation.
When evaluating platforms, organizations should prioritize:
- Compatibility with existing cameras and access control systems
- Open APIs and integration flexibility
- AI-driven analytics that surface actionable insights
- Centralized management for multi-site environments
This is where platform architecture matters.
How Lumana Supports Unified Video and Access Control
Lumana is an AI-native video security platform built to unify video surveillance, access control events, and real-time analytics into a single operational layer.
Rather than forcing organizations into proprietary hardware ecosystems, Lumana works with existing IP cameras and integrates access control data to provide immediate visual context for every access event.
Key capabilities include:
- Camera-agnostic architecture: Add advanced intelligence without replacing existing camera infrastructure.
- Real-time access event verification: Automatically link badge swipes, denied entries, and forced doors to live and recorded video.
- AI-powered behavior detection: Identify tailgating, loitering, repeated access failures, and other high-risk behaviors as they happen.
- Centralized, multi-site visibility: Monitor entrances, incidents, and trends across all locations from a single dashboard.
- Accelerated investigations: Search and reconstruct incidents in minutes using linked timelines and AI-driven video search.
By combining access control data with real-time AI video intelligence, Lumana helps organizations move from reactive monitoring to proactive risk prevention while maintaining flexibility as needs evolve.
Request a demo to see how Lumana unifies AI video security and access control to deliver real-time visibility at every door.
Frequently Asked Questions
What is the difference between integrated access control and standalone access control?
Standalone access control systems only grant or deny entry based on credentials, while integrated systems combine access control with video surveillance, analytics, and alarms into one unified platform that enables real-time verification and faster response to security events.
Can I integrate my existing access control system with video surveillance?
Yes, most modern access control systems can integrate with video management software through open APIs or third-party integrations, though compatibility depends on your specific hardware and software vendors.
Is integrated access control more expensive than standalone systems?
While initial setup costs may be higher, integrated systems typically reduce long-term operational expenses through unified maintenance, eliminated redundancy, and improved staffing efficiency.
What compliance standards apply to integrated access control systems?
Depending on your industry, relevant standards may include GDPR for data privacy, HIPAA for healthcare, PCI-DSS for payment processing, and local building safety codes that your integrator should help map to your system design.
Related Articles
Security management
Feb 12, 2026
How Access Control Systems Are Evolving With AI and Video Security
Security infrastructure
Feb 11, 2026
Beyond CCTV Systems Limitations: The Case for AI-Powered Security
Company
Feb 9, 2026





